After a name change and several company takeovers, you’ll be forgiven to think that HMA VPN – historically known as “HideMyAss” – is a refreshed VPN brand.
| Looking for better-rated VPNs? See our “Best VPN” list to find top services for speed, privacy and value. |
The truth is that HMA has been around longer than most personal VPNs.
But does that mean its service is still up to par with modern standards?
Is it a reliable and secure VPN to use? Is it based in a safe jurisdiction, and is it cheap?
To make an objective judgment on whether this VPN is worth buying, I tested HMA to get the real facts.
Here’s what I found out in my HideMyAss VPN review.
In this guide 🔍
- What is HMA VPN?
- How much does HideMyAss cost?
- Is HMA VPN safe?
- How does HideMyAss work?
- Does HideMyAss work with Netflix?
- Is HideMyAss any good?
- More HideMyAss FAQs
HMA overview
| Based in | United Kingdom |
| Price | $2.99 /mo. |
| Speed | 200 Mb/s |
| Logs | No (audited) |
| Apps | PC, Mac, Android, iOS, Linux, Android TV, Chrome, Firefox |
| Features | IP refresh, kill switch, split tunnelling, AES-256-GCM, free proxy |
| Works with | Netflix, Amazon Prime TV, Apple TV, PS4, Xbox, routers |
| Torrents | Allowed |
| Works in China | No |
| Connections | Up to 10 |
| Free trial | Yes |
| Refunds | 30 days |
| Customer support | Live chat, email, user forum |
| Website | HideMyAss.com |
What is HideMyAss?
HideMyAss – or HMA – is a VPN and proxy service based in the UK.
It has virtual private network apps for most operating systems and is compatible with many platforms for streaming or gaming.
The provider is well known for its enormous server network – which I’ll talk about more later in this HideMyAss review, and you’ll also find some useful security features built into its VPN clients.
HMA price & coupons
HMA offers three subscription packages depending on how long you want to sign up for.
You can choose between the 1, 12, 24 or the ‘recommended’ 36-month plan.
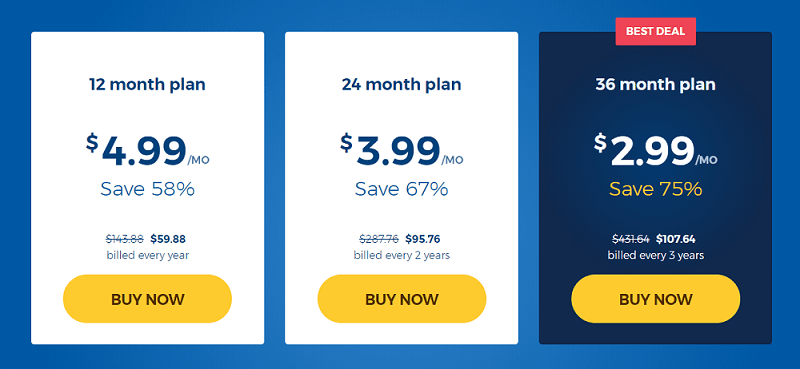
| 36 months | $2.99 /mo. (save 75%) | Get started |
| 24 months | $3.99 /mo. (save 67%) | Get started |
| 12 months | $4.99 /mo. (save 58%) | Get started |
| 1 month | $11.99 /mo. | Get started |
| 7 days (free trial) | Free | Get started |
Price-wise, you’ll pay about the average for any half-decent VPN.
But you will get a large discount on the lengthier packages. The 3-year plan, for instance, is discounted at 75% from HMA VPN labels as its standard price.
HMA has discounted options for students and businesses.
You can also buy HMA VPN for your family on a plan that allows up to 10 connections at one time.
At first, I didn’t think HMA offered a monthly subscription, but after some digging around, I found it. It shows up depending on which country you’re accessing HideMyAss.com from. But if you don’t see it immediately, you can change the website’s locale, and the monthly plan will become visible.
The 30-day money-back guarantee does offer some peace of mind though.
HideMyAss coupon – can I get a discount?
HMA often launches special offers, unique to the country you purchase it from.
Currently, you can get a discount for as much as 75% on the 36-month plan.
In that case, you’ll be saving a lot, and will have access to a paid VPN for a while.
You won’t need a coupon code in order to get this VPN deal.
Payment methods
HMA is fairly accommodating with payment options, allowing for PayPal, VISA, Mastercard, American Express and more.
| PayPal | ✅ |
| Credit card (Visa, Mastercard, American Express) | ✅ |
| Discover | ✅ |
| Google Pay | ✅ |
| Apple Pay | ✅ |
| Alipay | ✅ |
| Sofort Banking | ✅ |
| Boleto | ✅ |
| Hipercard | ✅ |
| iDEAL | ✅ |
| Cryptocurrency | ❌ |
However, you can’t pay for HMA using Bitcoin or other cryptocurrencies.
Speed – how fast is HMA VPN really? (200 Mb/s)
| When using HMA, you can expect your download speeds to comfortably reach up to 200 Mb/s; also depending on your own connection, of course. My speed test shows HMA is one of the faster VPNs you can find. |
The faster WireGuard protocol isn’t available with HideMyAss, so I used the default OpenVPN connection to check its speeds.
The results weren’t too bad at all.
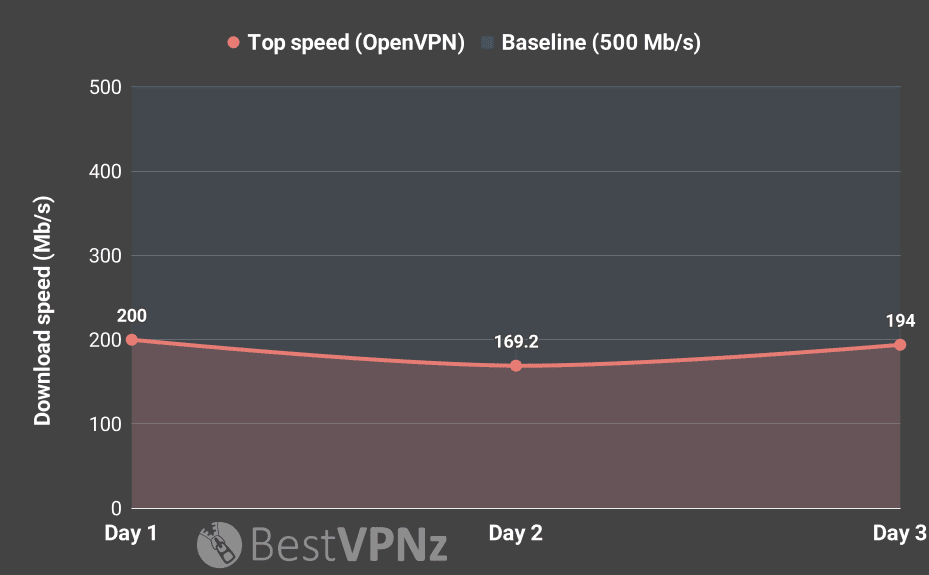
In fact, when comparing HMA’s top speed with other services, it actually scored as one of the fastest VPNs over OpenVPN.
The top download speed I clocked was 200 Mb/s using a nearby UK server.
HMA VPN speeds by location
| Server location | Top speed | Average speed |
| United Kingdom | 200 Mb/s | 187.7 Mb/s |
| Netherlands | 190.8 Mb/s | 178.4 Mb/s |
| US – New York | 88.3 Mb/s | 80.6 Mb/s |
| Canada – Toronto | 146.4 Mb/s | 143.7 Mb/s |
| Pakistan (virtual) | 38.2 Mb/s | 31.7 Mb/s |
| Singapore | 129.8 Mb/s | 109.1 Mb/s |
What’s better is that all but a couple of location managed to reach peak speeds above 100 Mb/s. And even up to 200 Mb/s, as you see with my local UK server.
That’s really good.
Although, I should add that the Pakistan node was actually a virtual location, not a physical node.
On average, the speed between all six locations over seven days of VPN tests was 122 Mb/s.
Generally, I’m impressed HMA VPN’s network performance with OpenVPN.
It would, however, be even better if the service offered WireGuard support which should see these speeds reach in excess of 300 Mb/s (based on my 500 Mb/s internet connection).
Is HideMyAss safe to use?
| HideMyAss is a verified no-log VPN. It passed all of my IP leak and security tests, meaning it’s overall a safe VPN to use. It’s also owned by the well-known cybersecurity company – Avast. The VPNs main downside is that it’s based in the UK, which is not regarded as a safe jurisdiction for privacy reasons. |
| No logs | ✅ |
| Safe jurisdiction | ❌ |
| Good track record | ✅ |
| AES-256-bit full-disk encryption | ✅ |
| No IP, DNS leaks | ✅ |
| No viruses or malware | ✅ |
IP / DNS / WebRTC leak test (passed ✅)
HideMyAss VPN passed the IP leak test, including for DNS and WebRTC leaks, with no identifiable markers showing up while I was connected.
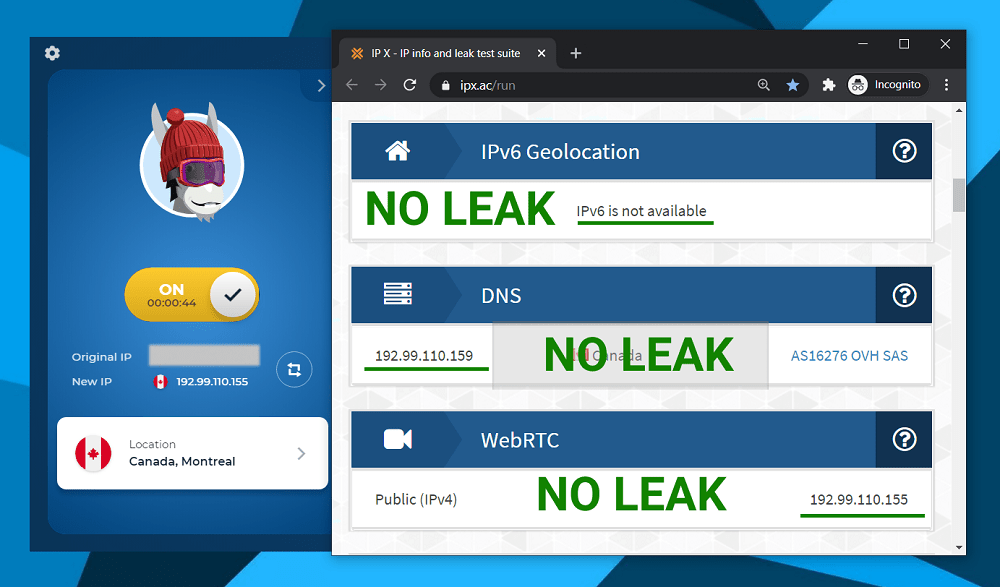
HMA doesn’t have an ‘IP leak protection’ option built into its VPN client, but states it does apply the added protection layer for all of the common leaks behind the scenes.
Virus scan (passed ✅)
I used my preferred virus protection tool – VirusTotal – to check HMA VPN Windows software for any security threats.
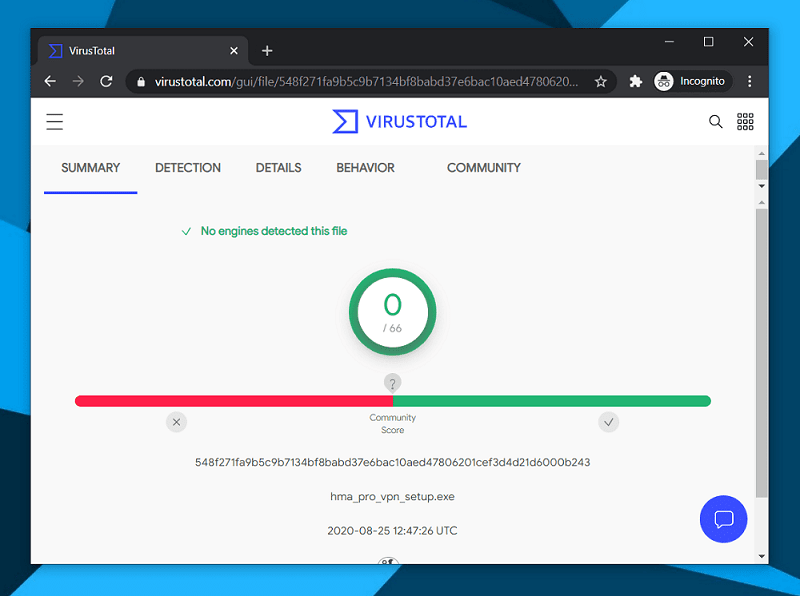
As you can see, the VPN client is free from viruses and malware, and is thus safe to install.
Deep packet inspection (passed ✅)
I’m happy to report that HideMyAss VPN passed my deep packet inspection.
After navigating to a few random sites while being connected to HMA VPN, I could see none of the sites’ addresses were leaked into data packets.
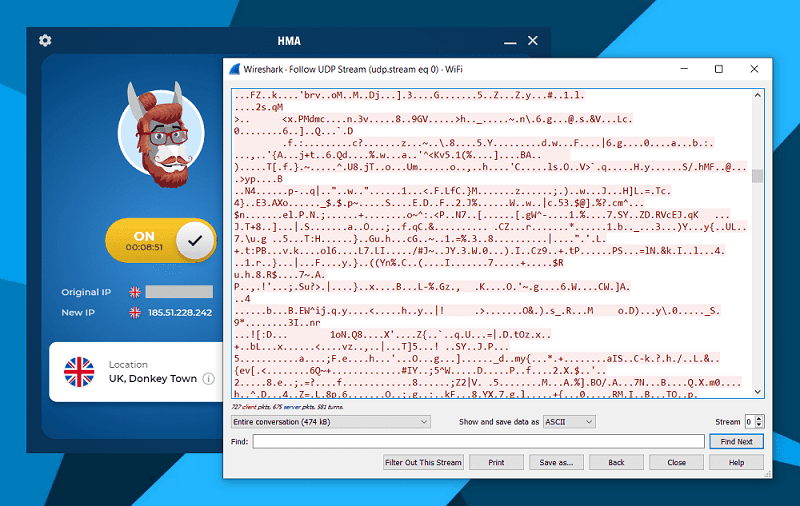
The output of these packets shows an incoherent mix of letters, numbers and characters, meaning this is what my ISP can see of my online presence when I’m using the VPN.
With no web activity leaking, I know my traffic stays encrypted while I’m connected.
Does HideMyAss VPN keep logs?
HMA’s strict ‘no-log’ policy is one of its main selling points.
But are its claims true?
A credible privacy policy is essential when considering buying a VPN. And HMA in particular is under the spotlight.
Why?
Because HMA used to store connection logs (transparently), and was once forced to hand over user information to authorities (see below on the HMA & LulzSec incident).
Today, however, the company claims to operate with a ‘no-log’ policy.
This means HMA doesn’t record IP addresses, DNS requests or your traffic data.
Our No Logging Policy – data we don’t send to our servers. Period: originating IP address; any DNS queries while connected; browsing history; transferred data
Excerpt from HMA’s privacy policy
This has been in place since April 2020. So if you weren’t happy with HMA VPN logging policy before, perhaps it’s worth taking a second look.
To be clear, HMA can’t claim that it doesn’t log any information at all, because it saves some non-identifiable data for 35 days before destroying it.
However, it only picks up the day of connection and a rounded figure for how much data was transferred (e.g. 2GB of data).
There’s comfort in the fact there are no detailed time stamps or logs of my activities.
Has HMA VPN been audited?
HMA VPN has had a privacy audit conducted, done by the cybersecurity consultancy – Verspite.
The audit verified HMA’s ‘no-log’ policy was accurate and the VPN provider did not store any more data than it advertises.
Its parent company – Avast – also publishes a transparency report on its website, however, at the time of writing this HideMyAss review, it was last updated in 2018.
HMA & the LulzSec incident
In 2011, Cody Kretsinger used HMA’s proxy service to hack into the Sony Pictures Entertainment website, leaking personal details of thousands of gamers on the Playstation network.
The incident was a high-profile data breach, and was covered extensively by global news outlets.
Leaked IRC chat records suggested the hacker group LulzSec was behind the attack, with some of the members claiming to have used HideMyAss VPN in the process.
An FBI investigation ensued, and HMA received a court order to provide information on its users.
It first came to our attention when leaked IRC chat logs were released, in these logs participants discussed about various VPN services they use, and it became apparent that some members were using our service. No action was taken, after all there was no evidence to suggest wrongdoing and nothing to identify which accounts with us they were using. At a later date it came as no surprise to have received a court order asking for information relating to an account associated with some or all of the above cases. As stated in our terms of service and privacy policy our service is not to be used for illegal activity, and as a legitimate company we will cooperate with law enforcement if we receive a court order (equivalent of a subpoena in the US).
Excerpt from HMA’s blog
As a result of HMA cooperating with US authorities, the user was identified through VPN connection logs.
Does this mean HMA told fibs?
The big question from all of this for me is – did HMA get exposed on false advertising and a misleading privacy policy?
After all, almost every report has since damned HideMyAss about handing over logs to a third party.
In reality, what a lot of these reports miss out – intentionally or not – is that HMA was already transparent about keeping connection logs (IPs and timestamps) for 30 days.
In fact, as a UK company, it had to, as it was subject to the now scrapped European Data Retention Directive.
Therefore, by law and per its terms, it had to cooperate with authorities as its service was used for illegal activity.
In my view, it’s safe to say HMA wasn’t exactly ‘caught out’ on misleading T&Cs. Unlike, say, PureVPN which, at the time of its 2017 connection logging incident, claimed to have only kept timestamps and bandwidth usage.
The only remaining concern is that HMA had kept any identifiable user logs at all.
But most VPNs did (and many still do).
Funnily, this incident was one of the main triggers for the ‘zero-logs’ trend among VPNs.
Who owns HideMyAss?
Originally, HMA VPN was named “HideMyAss”, when its founder – Jack Cator – needed a way to bypass his school’s firewall-protected network.
This took place in 2005 when Jack was only 16 years old and use of personal VPNs wasn’t as widespread as it is today.
During the past 15 years, the company has grown massively, and has seen some changes too.

First, HideMyAss became noteworthy in the VPN industry. After 10 years in the business, AVG acquired the business, and then in 2016, security giant Avast took over AVG.
So, HMA is now part of the publicly listed Avast group, which at least carries a positive reputation as cybersecurity specialists.
The downside to these events is that, for a while, as part of a bigger company, HideMyAss didn’t develop as quickly as some of its VPN competitors.
As a result, the once arguably largest VPN service has since been overtaken by the likes of ExpressVPN and IPVanish.
Lately though, there are various changes going on with the product – from rebranding to ‘HMA VPN’ to numerous service and hardware improvements.
Where is HideMyAss based?
HMA VPN is based in the United Kingdom (UK).
Sadly, this is not a good jurisdiction for a VPN service.
The legislation in the UK allows the government to subject telecommunications companies, including VPNs and your ISP, to serve notices requiring providers to retain data for up to 12 months.
What makes this possible is the notorious Investigatory Powers Act – otherwise dubbed the ‘Snooper’s charter’, which used to enforce mandatory data retention in the UK.
However, it was revised with the 2018 Data Retention and Acquisition Regulations amendment, which now requires the government to serve companies with individual notices based on specific criminal investigations.
How this potentially clashes with HMA’s ‘no-log’ is not entirely clear.
I contacted HideMyAss for clarification, and they stated:
Changes to our infrastructure make it impossible to start logging and retain any identifiable data.
HideMyAss representative
Avast transparency report
Avast does publish a data request transparency report, covering its main products, including HMA.
At the time of writing this HideMyAss review, the report shows HMA has complied with government-issued requests for user data up to 2018.
The data it provided until then includes IPs, emails and billing information.
We have had 102 requests from law enforcement agencies. The countries that requested data for criminal investigations were United Kingdom (71 requests), United States (13 requests), Spain (4 requests), Germany (3 requests), Austria (1 request), Chile (1 request), Czech Republic (1 request), Estonia (1 request), France (1 request), Hungary (1 request), India (1 request), Italy (1 request), Norway (1 request), and Portugal (1 request). From these requests, we disclosed data 39 times in the United Kingdom and 1 time in the United States. The data we disclosed in these instances were root IP addresses, email addresses and billing information.
Source: Avast transparency report
However, the report hasn’t been updated since 2019, so it’s not obvious how HMA complies with data requests today.
Especially with its new ‘almost’ no-log policy.
The fact that it has been audited is a huge plus. But UK’s draconian surveillance and data retention laws are a cause for concern.
How does HideMyAss work?
| HMA VPN is very much built to be a user-friendly privacy tool. Its VPN apps are extremely simple and easy to navigate and I doubt you’d get lost when customising your connection. It works with many services like Netlix and it’s also a VPN you can use for safe torrenting. Its huge server network allows you to connect to almost any virtual location in the world. HMA also offers a free proxy service. |
| Servers | 1,100+ |
| Apps (PC, Mac, Android, iOS, Linux) | ✅ |
| Torrenting | ✅ |
| Works with Netflix | ✅ |
| Works in China | ❌ |
| Max. connections | Up to 10 |
HMA VPN apps & compatibility
I must say, when it comes to compatibility, HMA stays true to its claims.
It offers VPN apps for PC, Mac, Android and iOS/iPhone users with which you can quickly connect to its service.
| Windows | ✅ |
| macOS | ✅ |
| Android | ✅ |
| iOS | ✅ |
| Linux | ✅ |
| Android TV | ✅ |
| Amazon Fire TV | ✅ |
| Chrome / Firefox add-on | ✅ |
| Router support | ✅ |
| Gaming consoles | ✅ |
There’s even a quick way to configure it on your Apple TV and Android TV.
HMA also works with certain routers. It may be tricky to configure these but it does provide extensive guidelines to help users with setup.
Remember, you can’t use HMA on just any router. The router must support VPNs or it must be flashed, either with DD-WRT, Tomato or other compatible firmware.
Desktop client (PC)
The first thing that comes to mind when I consider HMA is the dashboard is much less intimidating than some other VPNs I’ve tested. The UX feels intuitive.
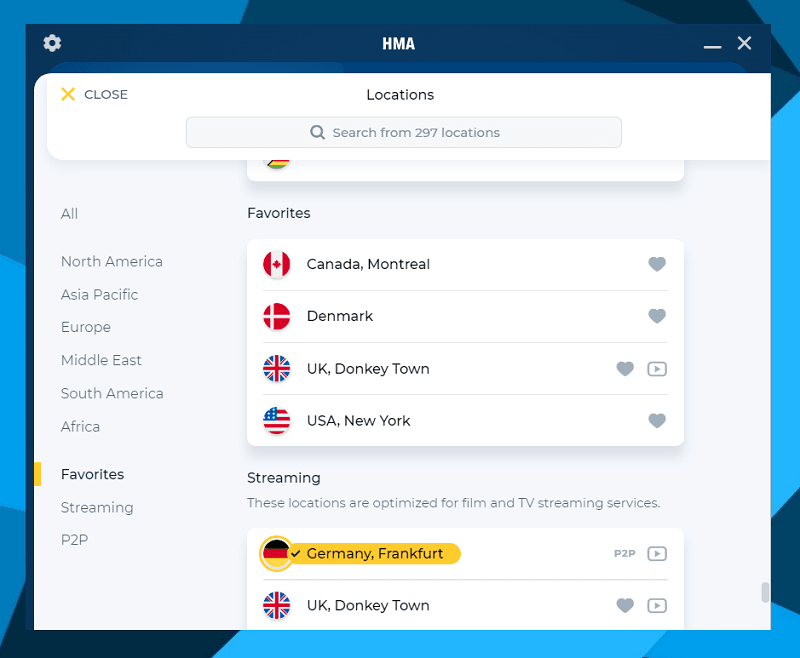
Even a newbie should be able to understand the user-friendly layout, feature descriptions and the privacy settings.
It’s also visually appealing and provides necessary information in clear tables, images and toggle switches. For example, the HMA VPN country list – grouping server locations by continents.
Additionally, you can bookmark your favourite locations and quickly jump to the specially designated nodes for streaming or torrenting.
Mobile apps (Android & iOS)
The mobile app is as easy-to-use as the desktop version. Just remember there are limitations depending on whether you’re working on Android or iOS.
I mention some of them later in this HideMyAss review.
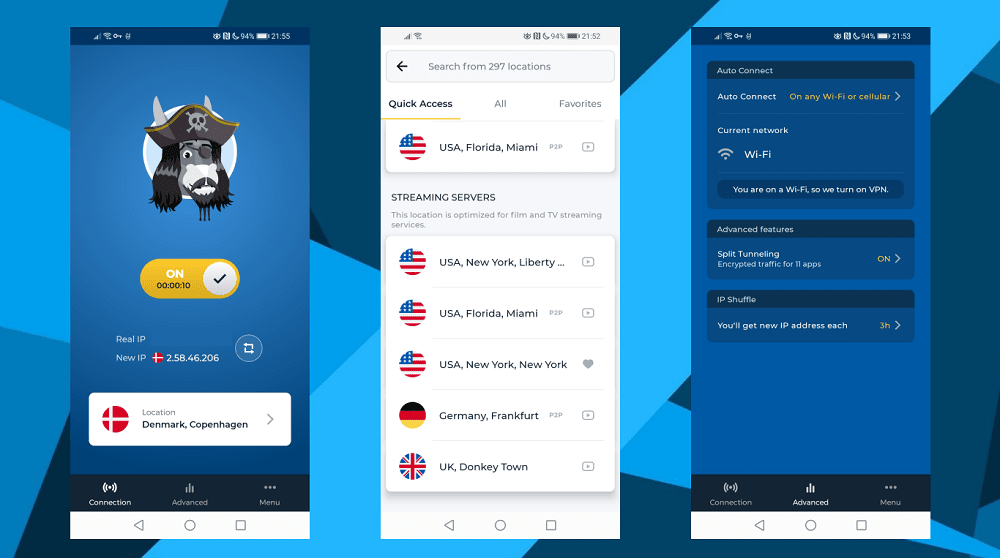
Like the desktop client, the HMA mobile app isn’t really feature-rich. But the basics are in place.
Yet what I didn’t really like was that my bookmarked server locations from the desktop client did not sync to the mobile app.
Linux client
The Linux client is a bash script, which I think is brilliant.
This enables the user to easily review the script to be sure nothing weird is going on.
As well as ensuring portability across architectures, as long as the required programs are installed, it allows you to use the open source OpenVPN binaries. The value add comes with the script downloading HMA’s configuration files and the straightforward user interface.
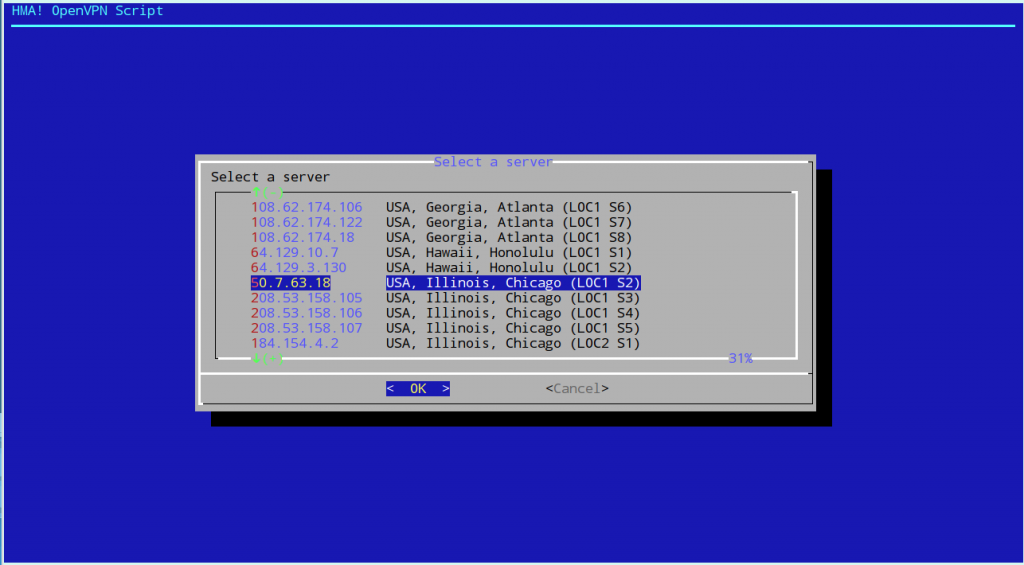
Where are HideMyAss servers?
Here’s a big selling point of HMA, and I must agree it’s an attractive feature: the product really does have an impressive list of servers.
HMA has gateways in 190+ countries, in 290+ locations, clustering 1,100+ servers.
Nodes are located all across the globe.
HMA actually has a unique way of looking at these locations by using ISO country codes as references.
With this approach, there are actually 200+ virtual countries available. More than advertised.
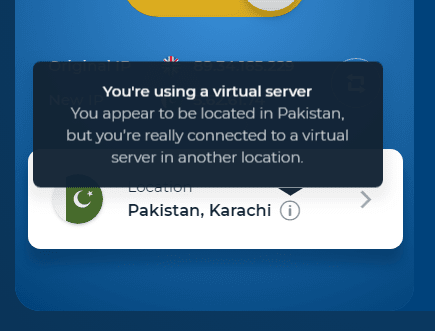
Does HMA use virtual server locations?
HideMyAss’ large network of servers includes both physical and virtual servers.
But, I do think HMA should improve on how virtual servers are labelled on the website and in the app.
Currently, you can see which locations are virtual only after connecting to the VPN.
Is HMA VPN secure?
Next, I’ll run through HMA’s security features:
| RAM-based servers | ❌ |
| Kill switch | ✅ |
| IP leak protection | ✅ |
| IP shuffle | ✅ |
| Custom DNS | ✅ |
| Split tunnelling | ✅ |
| Obfuscation | ❌ |
| Multi-hop | ❌ |
| Tor over VPN | ❌ |
| Ad blocker | ❌ |
Encryption
HMA implements varied levels of encryption, depending on the device you’re connecting from.
On Windows and Android you’ll connect with the OpenVPN protocol by default, using AES-256-GCM encryption, OpenSSL with RSA 4096-bit keys for handshakes and SHA256 for authentication.
Its current OpenVPN configuration is definitely an upgrade from the previously implemented 128-bit Blowfish-CBC cipher, which is nonetheless secure, but is generally regarded as less efficient than AES.
If you’re using Mac or iOS, HMA takes a different approach, using IKEv2/IPSec, still with 256-bit Advanced Encryption Standards.
Does HideMyAss support WireGuard?
HMA doesn’t yet support the WireGuard protocol, which some users may find frustrating.
While WireGuard is still a protocol in development, some VPNs are already rolling it out on their services.
That said, HMA is still a fast VPN through OpenVPN. You shouldn’t have recurring problems with connectivity.
Kill switch
HMA provides the handy internet kill switch, and it’s your prerogative whether you want to use it or not. But for privacy purposes, I would definitely recommend keeping it on.
After all, any VPN server can be prone to unexpected disconnections.
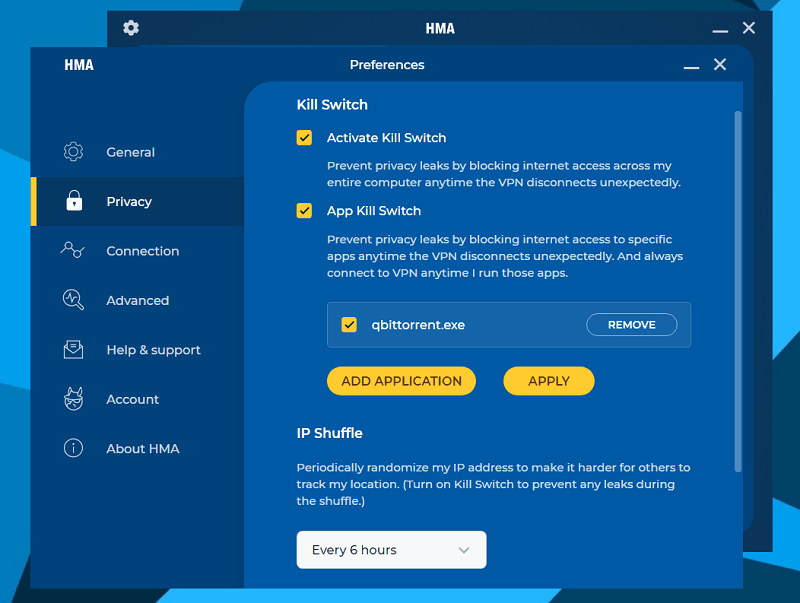
HMA also has a kill switch for specific applications.
Currently, the feature isn’t available on its mobile client
Split-tunnelling
HMA comes with split-tunnelling, which lets you run specific apps through the VPN rather than your entire device.
One drawback to this feature – it’s only available on Android.
IP shuffle & refresh
One of the nifty tools that’s on hand in your dashboard is IP refresh, which assigns you a new VPN IP in the same location you were already connected to.
This feature is useful in case your current VPN IP is blocked by certain websites and you quickly need a new one without having to manually reconnect to another server.
Simply hit ‘refresh’ and you’ll have a new IP address for the same virtual location as before.
You can even set the app to automatically refresh the IP after some time has passed.
This is great for security, but make sure to have the kill switch switched on for backup.
Can I connect multiple devices at once?
HMA VPN allows up to 5 simultaneous connections on standard plans.
However, with the family plan you can connect up to 10 devices.
Is HMA safe for torrenting?
HideMyAss allows torrenting on its service, and has multiple servers dedicated specially for P2P.
These are clearly labelled in the HMA client, and there are 6 country locations to choose from – Germany, France, Czech Republic, UK, US and the Netherlands.
To ensure HMA is actually safe for torrenting, I ran a quick IP leak test on ipleak.net
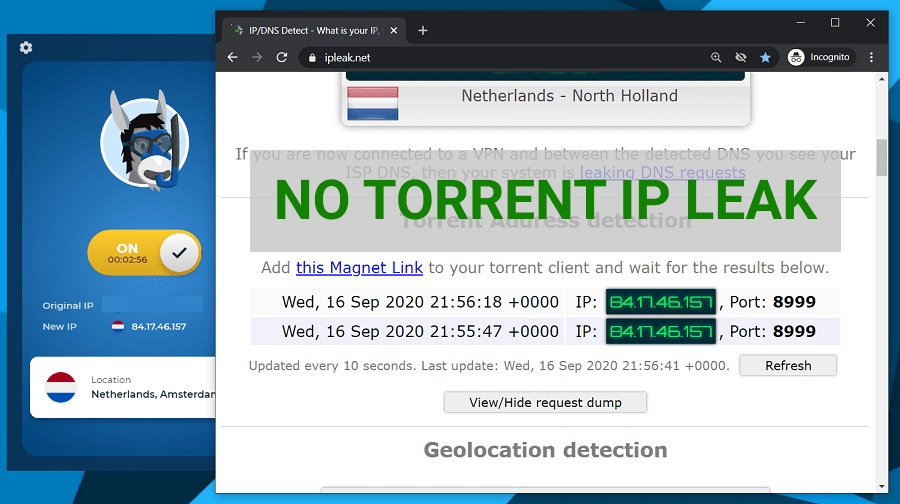
As you can see, my torrent IP reflected my VPN IP address in the Netherlands.
This means my real IP wasn’t leaking and proves HMA can be safe to use for torrents.
Does HideMyAss work with Netflix?
HMA has servers optimised for video streaming services. It doesn’t specify exactly for which ones, but the locations optimised include US, UK and Germany.
I tested to see if Netflix works with HideMyAss when connected to a US server, and, as you can see, the result was successful.
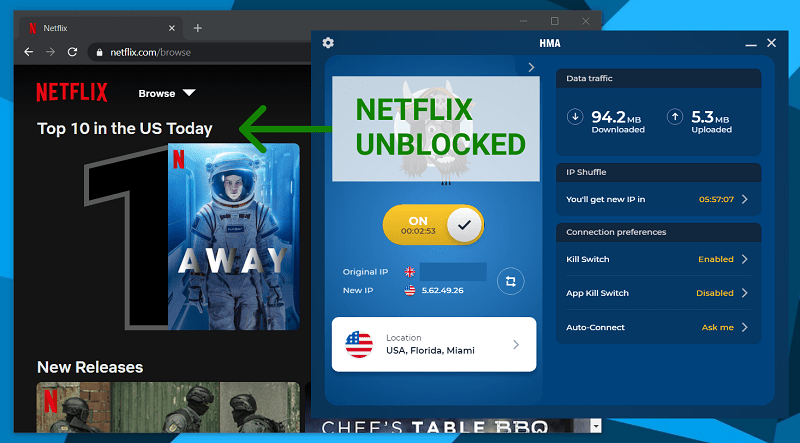
Netflix can unexpectedly give out an error if it picks up you’re using a VPN.
It gave me this error when I disconnected from the VPN. But the moment I reconnected to a US server with HMA, I had no issues with accessing international Netflix libraries.
The streaming quality was good, with no lag that I could notice.
Does HMA VPN Work in China?
HMA is not a reliable VPN to use to access the internet in China.
In the past, users have claimed to have had mixed success with bypassing China’s strict firewall rules. But nowadays, you’re not guaranteed good results.
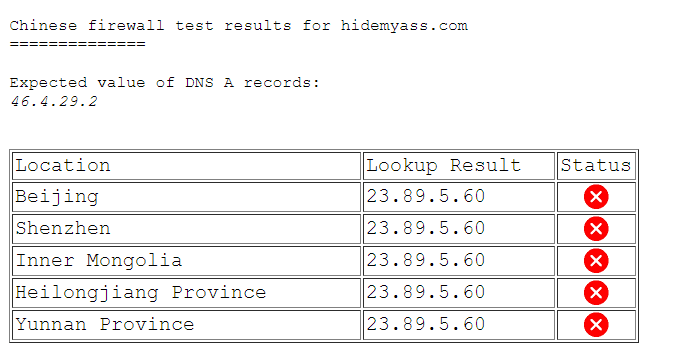
In fact, because HideMyAss has been around for many years, its main domain (HideMyAss.com) has long been blocked in mainland China.
Additionally, I couldn’t find any HideMyAss China mirror URLs for even accessing its website from within the country.
HideMyAss proxy – web & extension
Aside from its VPN, HideMyAss is also well known for its free web proxy – a cool feature HMA at one stage took away.
The proxy lets you spoof your IP address to one of five countries with your internet browser.
If you’ve used it before and have missed it, the proxy is now available again.
There are a two ways to access HMA’s free proxy.
It’s available as an extension for Firefox and Chrome browsers.
Alternatively, you can access it through HMA’s website where you can select your location, enter your web destination and the proxy will work much like a browser toolbar (not the retro, spammy kind).
You can connect to UK, US, Netherlands, Germany or Czechia.
The proxy also comes with some improved security features.
For example, it now encrypts URLs in your browsing history, in case you weren’t using incognito mode. It also blocks cookies.
It’s generally a good option for streaming or accessing certain geo-restricted web content, minus the privacy aspect of the VPN.
HideMyAss reviews on Reddit (mixed)
A quick search for HideMyAss VPN reviews on Reddit, and you’ll find feedback that’s either mixed or leaning towards negative.
HMA is generally not recommended by the Reddit community, and this is mainly because of the LulzSec logging incident which I already mentioned earlier in the review.
Some users have also reported problems with accessing websites because of dirty IPs assigned by the VPN.
This is the result of certain servers being abused, which usually happens when too many users are connected to the same VPN.
I’ve used Hide My Ass on an off over the users and every time I try to use their paid VPN service I am unable to access most of the sites I visit on a regular basis, Google, forums. All I get is a blank, white screen. Although, sometimes when visiting a forum I might get a message saying my IP has been banned.
Source: Reddit
Many Reddit threads about HideMyAss are actually quite old, and this is most likely because of the rise of other VPNs over the past few years.
HideMyAss vs NordVPN
Let’s get some perspective by comparing HMA with a market leader like NordVPN.
| HMA VPN | NordVPN | |
| Price | $2.99 /mo. | $3.71 /mo. |
| Top speed (OpenVPN) | 200 Mb/s | 373 Mb/s |
| Logs | Connection (audited) | None (audited) |
| Servers | 1,000+ in 190+ countries | 5,000+ servers in 50+ countries |
| Works with Netflix | ✅ | ✅ |
| Works in China | ❌ | ✅ |
| Torrents | ✅ | ✅ |
| No IP / DNS leaks | ✅ | ✅ |
| Connections | 10 | 6 |
| Support | Live chat, phone, email | Live chat, email |
| Website | HideMyAss.com | NordVPN.com |
NordVPN is noticeably a more trusted VPN thanks to its multiple audits and the company’s location in data retention-free Panama.
On the other hand, HMA has its own benefits like the initial free trial as well as its mega-sized gateway network.
All features considered, I am giving my thumbs up to NordVPN having confirmed it’s one of the fastest VPNs available.
Additionally, because NordVPN is based in Panama, I consider it a better option for your privacy.
🏆 Winner: NordVPN
Learn more about NordVPN and its features in our NordVPN review.
HideMyAss vs PureVPN
HideMyAss often gets compared with PureVPN. Here’s how these VPNs stack up head-to-head:
| HMA VPN | PureVPN | |
| Price | $2.99 /mo. | $6.49 /mo. |
| Top speed (OpenVPN) | 200 Mb/s | 144 Mb/s |
| Logs | Connection logs (audited) | No logs (audited) |
| Servers | 1,000+ in 190+ countries | 2,000+ in 140+ countries |
| Works with Netflix | ✅ | ✅ |
| Works in China | ❌ | ✅ |
| Torrents | ✅ | ✅ |
| No IP / DNS leaks | ✅ | ❌ |
| Connections | 10 | 10 |
| Support | Live chat, phone, email | Live chat, email |
| Website | HideMyAss.com | PureVPN.com |
HMA VPN is clearly the faster VPN, though the difference is probably not going to be noticeable.
Although PureVPN likewise boasts a large server network, HMA offers access to a lot more locations.
Both VPNs work with Netflix and other streaming services as well as torrents.
Likewise, both providers had previously been involved in high-profile logging cases.
🏆 Winner: HideMyAss
But the key difference is – HMA VPN is undoubtedly the more secure option.
This is because the UK-based VPN did not get caught out on false ‘no-log’ advertising, and it is clean of DNS leaks. Unfortunately, I can’t say the same about PureVPN.
HMA support – how to contact the provider
With HMA, you can easily navigate to find support, whether you’re on the website or using the app.
Your options are:
- Live chat & chatbot
- Phone support
- Email support (by submitting tickets)
- User community forum
- Online knowledge base
Chat support is available 24/7.
Using the automated chatbot, I found it helpful that it already lists useful information on certain topics. These are mostly about accounts and billing – or purchasing HMA.
But I also spoke to a HMA support agent about a brief connection issue I encountered.
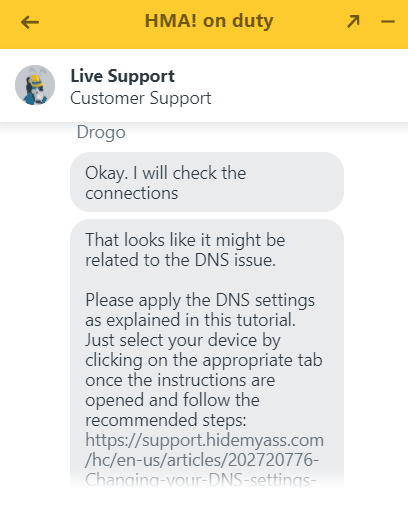
I was able to connect to the VPN, but couldn’t open any website in the browser – indicating a DNS issue.
The live chat agent immediately responded to my query, providing some helpful links and a step-by-step guide on how to resolve my issue. It turned out I needed to reset my own DNS settings.
As a follow-up, HMA also sends you a transcript of the chat, which is handy for future reference in case the issue occurs again.
When opening an email support ticket, you can attach files to better describe the issue.
HMA has a wealth of helpful online resources, technical guides and even an online community where you can check for product announcements and queries raised by other HMA users.
HideMyAss phone number
HideMyAss offers international phone support, but the number is difficult to find anywhere on its website.
Phone support is mainly reserved for new customers, which is why you’ll find the contact numbers only on the HMA checkout screen.
- International: +31 88 000 00 08
- US & Canada: +1 (650) 963 57 01
- Romania: +40 31 7101611
HideMyAss review – my conclusion (⭐ 7.4 / 10)
| There are many reasons why I can recommend HMA VPN. Based on actual tests, it’s a fast and secure VPN service. It’s also very easy to use, works with streaming services and allows torrent traffic on its network. One of its biggest perks is the sheer number of locations to choose from on its giant server network. |
The main downside for me with HMA is the fact it’s based in the United Kingdom. UK’s stringent anti-privacy laws make it a poor jurisdiction for VPNs.
However, HMA is adamant these laws won’t affect its verified no-log policy.
Is HMA perfect? Definitely not.
That said, I can’t but respect a VPN that is so user-friendly.
See my summary for a quick refresher on what you’ll invest in with HMA VPN:
Why HideMyAss is great 👍
- No traffic logs as audited by a third party
- Strong security features including full-disk AES-256-GCM encryption
- Fast speeds of up to 169 Mb/s
- Huge server network: 290+ locations give users excellent coverage across the globe
- Optimised for streaming with services like Netflix
- Allows torrenting through designated P2P nodes
- Nice apps for all operating systems
- Good support options including phone support
- Free trial for 7 days
- Free proxy extension for Chrome and Firefox browsers
Why consider alternatives 😬
- UK jurisdiction – bad for privacy
- Doesn’t work in China
- No kill switch on mobile
Is HideMyAss a good VPN?
Still, it’s encouraging to see HMA continually upgrading its product and its infrastructure. In an ever-changing VPN landscape, this sparks some trust.
It’s easily one of the cheaper VPNs based on its heavily discounted 3-year offer. Plus, the money-back guarantee means signing up to HMA is risk-free. All in all, it’s a decent VPN, especially for beginners.
The donkey is worth putting on your list of considerations.
HideMyAss alternatives
| I can recommend two alternatives to HideMyAss in case you’re not convinced on its privacy or perhaps there’s a missing feature that you really need. |
ExpressVPN
Pros
- Zero logs (verified)
- Safe jurisdiction (BVI)
- Fast speeds
- Excellent security features
- Works in China
- Allows torrents on all servers
- Slicks VPN apps
- Includes browser proxy
Cons
- Pricey
Private Internet Access
Pros
- Phenomenal speeds
- Proven 'no-log' claim
- Advanced security features
- Allows torrents
- Beautiful apps
- Secure browser extension
- Cheap subscription price
Cons
- Based in US (part of Five Eyes)
- Blocked in China
ExpressVPN is the VPN I’d recommend as an alternative to HMA for overall privacy, security and reliable performance.
There really aren’t many faults with it other than the price, which makes it one of the most expensive VPNs around.
Private Internet Access (or ‘PIA‘) is another hugely popular service.
Like ExpressVPN, PIA offers top security features and is a true, verified no-log VPN.
PIA’s main drawback is that it’s based in the US, meaning it can become subject to mandatory data retention at any time, and the public is unlikely to even find out about it due to anti-privacy laws like the Patriot Act and FISA.
That aside, PIA is otherwise an excellent VPN product with strong, built-in security features, and it’s also great for streaming.
HideMyAss review FAQ
What is HMA VPN?
HMA VPN is an acronym of HideMyAss, which — as you’ve probably figured out by now — is a VPN service. But aside from VPN, HMA also offers a free proxy solution.
Does HideMyAss work in iPad?
HideMyAss is fully compatible with iOS devices, and if you have a HMA subscription, you’ll be able to access its iOS VPN app — which works on iPads as well as iPhones.
Can I use HideMyAss in China?
Unfortunately, HideMyAss is not one of the services that will work in China. That said, there is no commercial VPN that’s guaranteed to work in the country consistently, over lengthy periods of time.
Is HMA VPN free?
HMA is a paid VPN service that offers several subscription plans depending on how long you wish to sign up for. HideMyAss doesn’t offer a free VPN plan, however, does have a 7-day free trial.
How much is HMA VPN?
HMA VPN pricing starts at $11.99 for the one-month plan. However, the monthly equivalent price drops significantly the longer you signup for. For instance, the yearly plan costs $4.99 per month, and that would save you 58% from the original price. Keep in mind that the discounted plans require an upfront payment.
Leave your HideMyAss review
Are you a HideMyAss customer or have used the service in the past?
Share your experience with us and leave your HMA VPN review and rating in the comments below. 👇



Still the VPN with the most locations.
Hide my ass is not bad. I don’t know why you gave it such a low rating. I have been a customer for a few years and with the exception of a few rare connection cut outs, this VPN is the most stable one I have used.
Hey – thanks for sharing this informative review!
One thing confuses me though, you’re stating
“HMA! supports OpenVPN over TCP but only on Linux or through the open source OpenVPN client.”
In fact, HMA offers OpenVPN-TCP and UDP, both can be used on any device/OS that supports OpenVPN.
In their software, UDP is called “auto-path” (it’s a setting in a separate tab).
Without their software, both, UDP+TCP can be used with any OpenVPN client and their config files from https://www.hidemyass.com/vpn-config/
Maybe you want to add that to the article :)
Greetings!
Hi Pete,
Thanks for sharing this information. I hadn’t looked into detail on what exactly it was the “auto-path” feature does. I was looking at the logs, and noted the client was connecting via UDP, but that is because I had the “auto-path” feature enabled! :)
I have since verified this with tech support. It also appears that their Android app is connecting via OpenVPN-TCP by default. Of course, like I mentioned, you can use the open source OpenVPN client and HMA!’s config files to connect via UDP or TCP.
Thanks for pointing this out. I will edit the review to reflect this. I just did a couple of quick speedtests and interestingly TCP is benchmarking better than UDP. Which is very unusual, because of the “TCP meltdown” effect. I didn’t include any OpenVPN-TCP benchmarks in the article, but if I get a chance I will go back and add a few.
Thanks again for sharing!
Was a bit apprehensive with HMA at first, but decided to try for one month (initially). I am getting 25 Mb per second out of 30 Mb to a server around 300km away. Faster than my previous two services.
Hidemyass worked perfectly when I needed to use public wifi in a hotel in Greece. Choice of servers won me over pretty quickly.
Which VPN protocol do you recommend that I use? I don’t understand the difference between PPTP and L2TP etc..?
PPTP is generally the fastest protocol but with the weakest encryption, while L2TP has better security and isn’t far behind PPTP in speed. Check our page that describes VPN protocols in detail: https://www.bestvpnz.com/vpn-protocols/
Works perfectly, my IP changes when I choose different servers! Their chat support is useful, answered all my questions. Thumbs up for Hidemyass
Finally I found a VPN with Sweden servers!
I’m not a pro with computers and was glad that HMA have their software, it made it very easy to connect the VPN
nice xmas deal! HMA’s software made the setup quick and easy
I got a very good price thanks to the xmas discount. I’ve connected two computers, including the one that my son uses. It’s comforting to know that the browsing data in my home is anonymous. HMA software made it very easy to setup the VPN.